AWS Setup
Setting up a server on AWS using Taskforger involves several steps to ensure a smooth and secure deployment. Below is a detailed guide on how to configure your AWS environment with Taskforger.
We provide integrations and a pre-configured image to handle much of the heavy lifting.
Prerequisites��
Before you begin, make sure you have the following in place:
- AWS Account: If you don't have an AWS account, create one here.
- AWS CLI: Install the AWS Command Line Interface by following the instructions in the AWS CLI User Guide. Taskforger relies on the setup process from the AWS CLI, so ensure it is configured correctly.
- Taskforger Desktop Client: Run Taskforger from the desktop client.
AWS Configuration
Local Machine Configuration
On your local machine:
- AWS Config: Configure your AWS settings, including the AWS regional zone. Follow the instructions in the AWS CLI Configuration Guide.
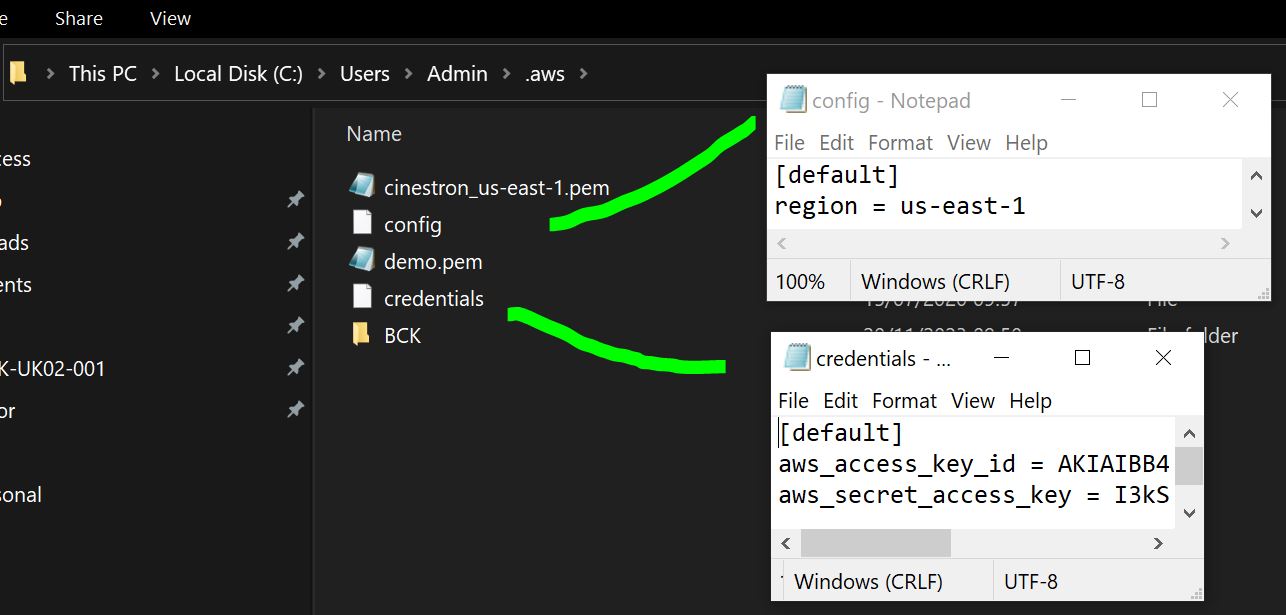
If you prefer not to install the AWS CLI, it may be possible to configure the settings correctly within Taskforger.
Secrets Manager
Utilize the AWS Secrets Manager to enhance security by setting your domain password. This ensures that sensitive information is not shared directly on any machine and allows secure connections to the domain of your PDC.
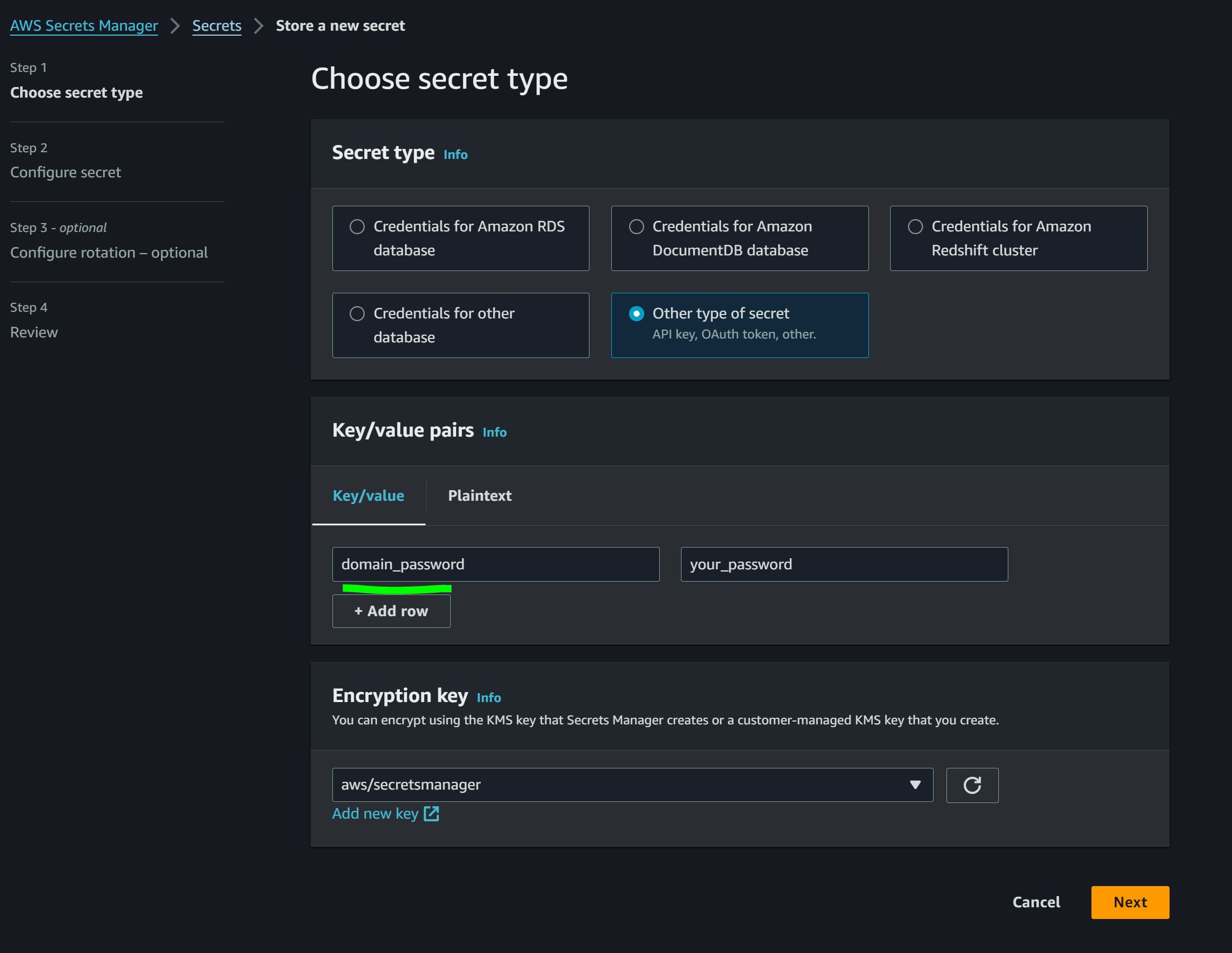
- On AWS, navigate to AWS Secrets Manager.
- Create a secret with the name "domain_password," containing a string value.
IAM Role
Create an IAM role on AWS for EC2 instances to read from the Secrets Manager.
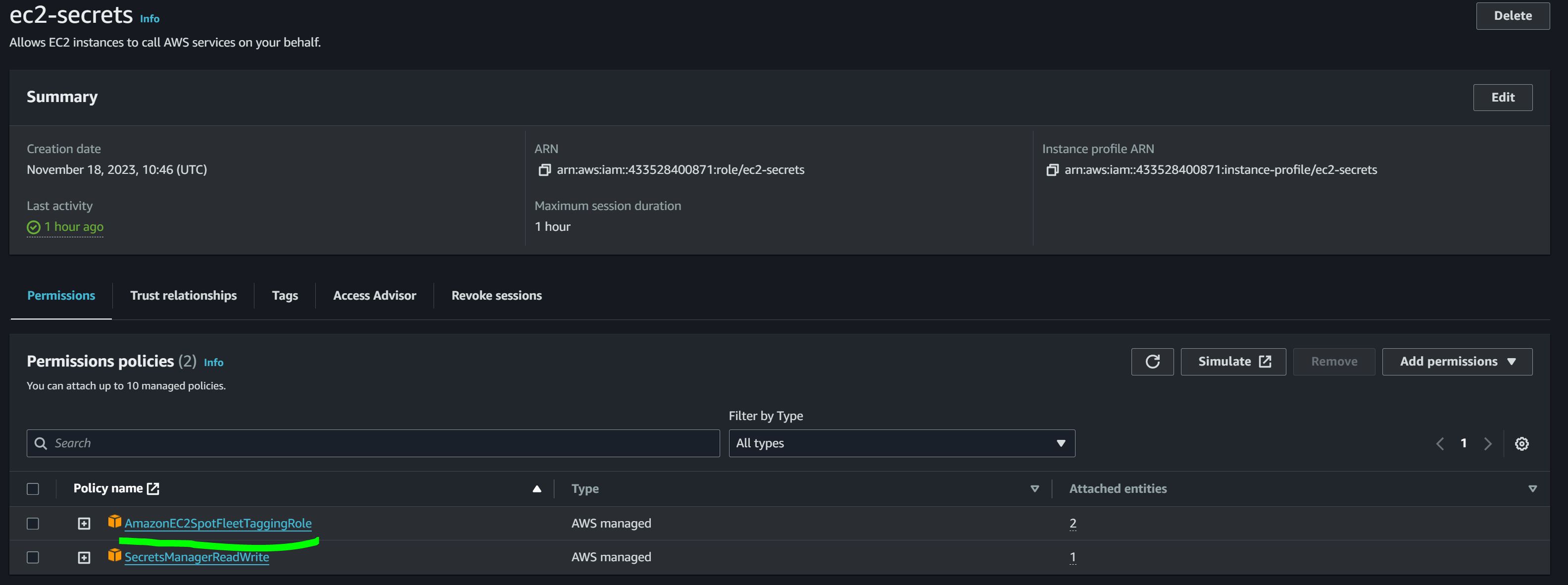
- On AWS, create a custom policy or use the built-in 'SecretsManagerReadWrite.'
- Required to connect to the domain.
- On AWS, create a custom policy or use the built-in 'AmazonEC2SpotFleetTaggingRole.'
- Required to update the instance name to match the internal computer name of terminals.
- This is formed by trimming the instance_id to the 15 char limit of Windows computer names.
This IAM role will be attached to launch templates in later steps.
Create Security Groups
In Taskforger:
- Navigate to the servers tab and right-click to access - Create - Default Security Group.
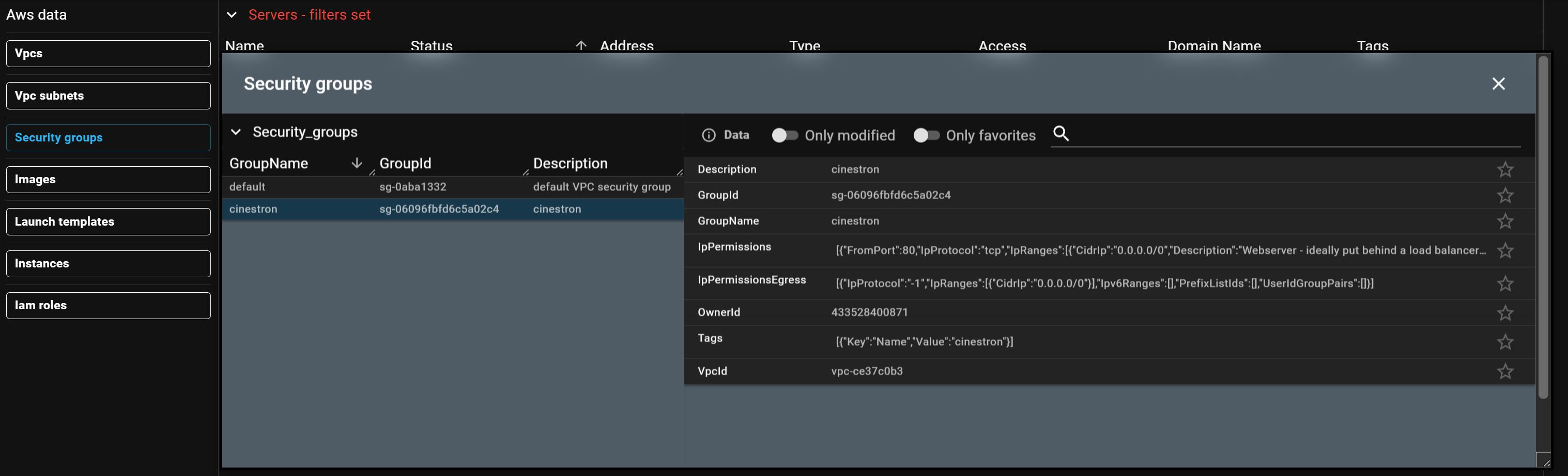
View security groups from inside Taskforger and on AWS. Note that all traffic is allowed between machines on the same security group within AWS.
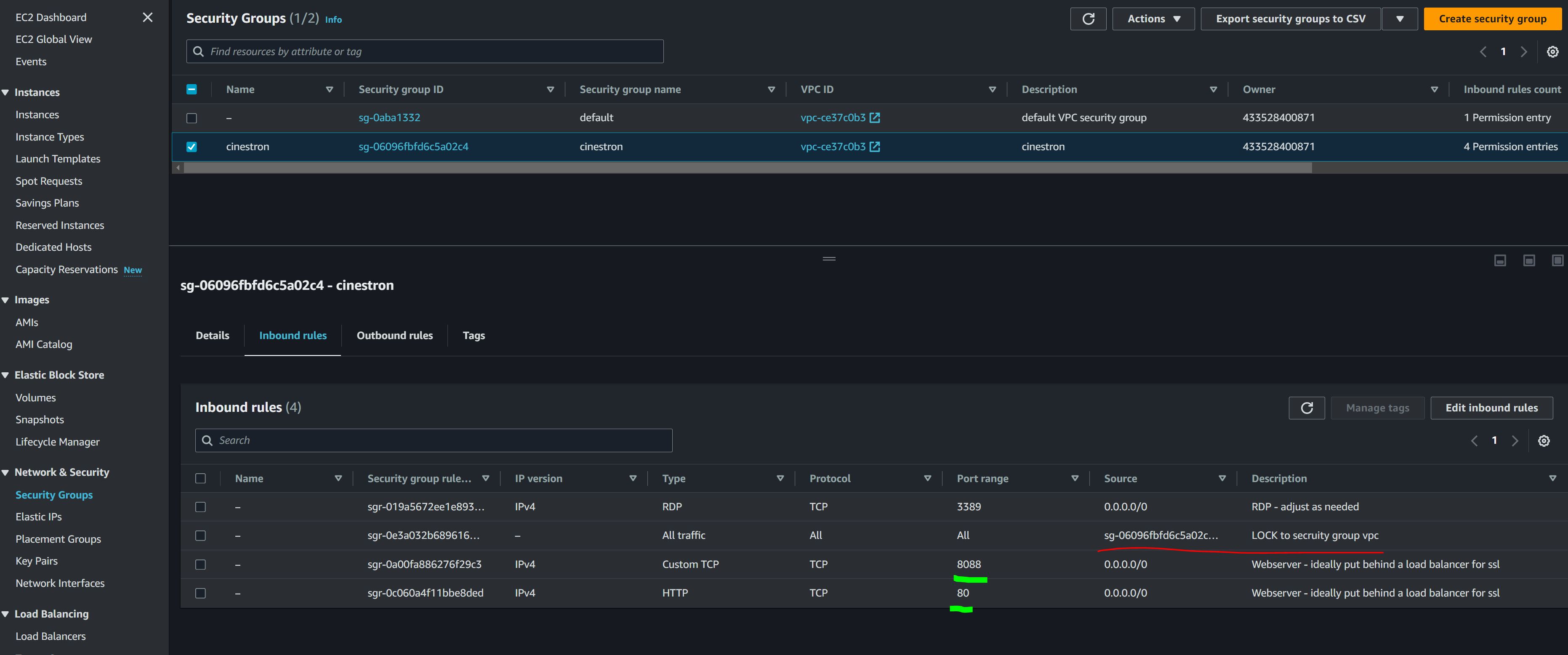
Consider implementing SSL and HTTPS for any access outside the internal AWS network.
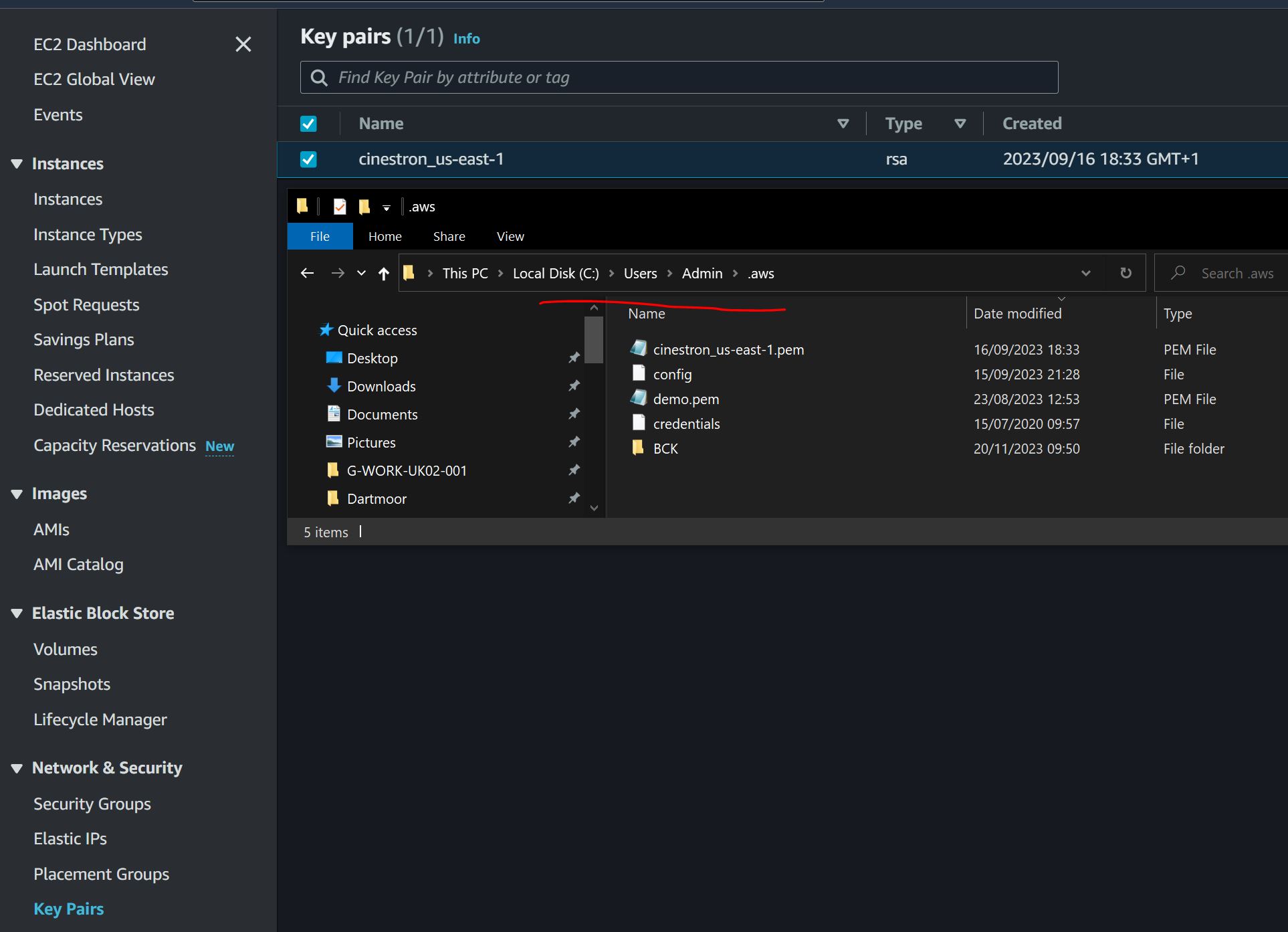
Key Pairs
A key pair .pem file will be generated with the organization and region settings. Safeguard this file as it is the only way to obtain the initial Admin password for any instances.
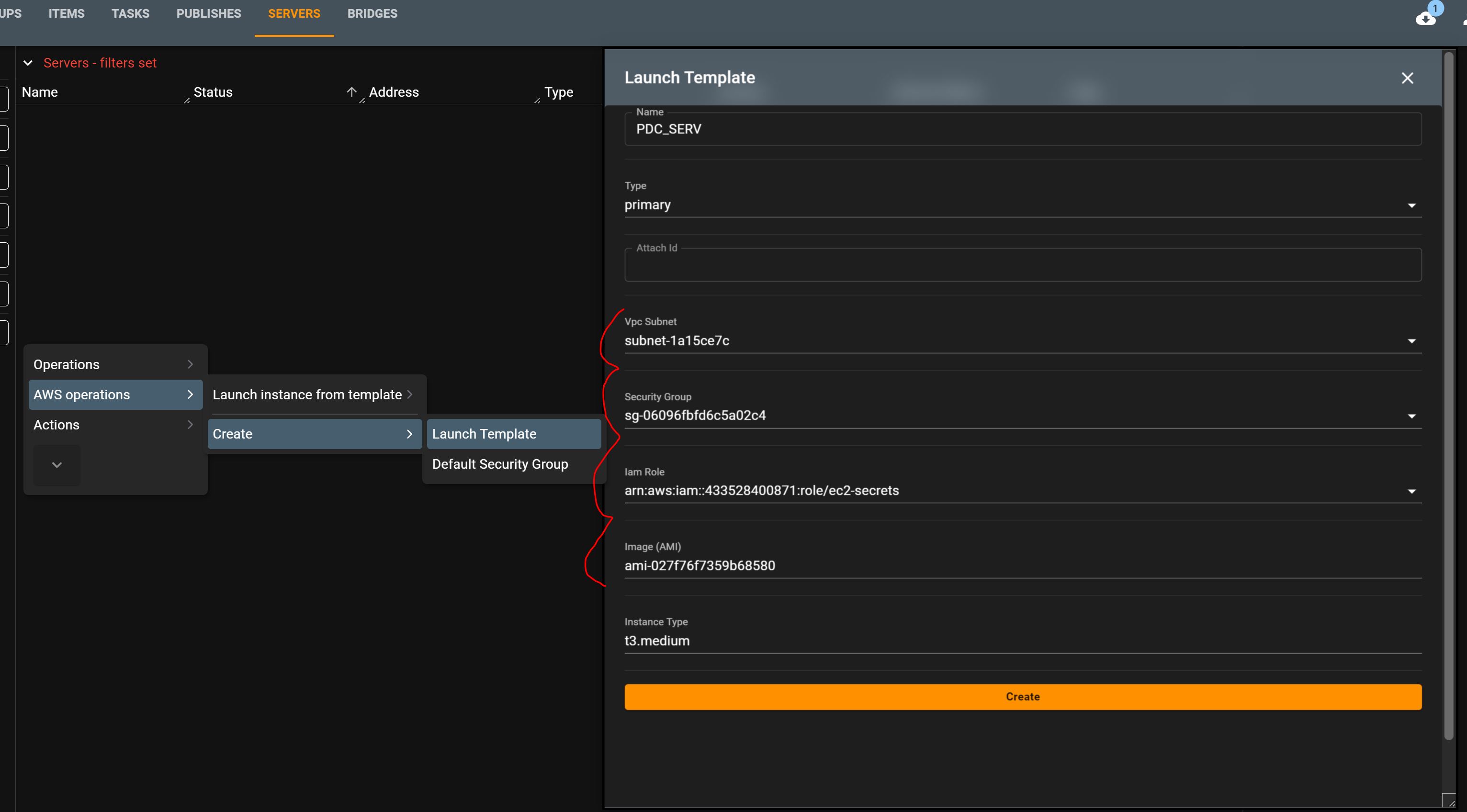
Create PDC Launch Template
To create a launch template for the Primary Domain Controller (PDC):
-
Right-click to access - Create - Launch Template.
-
Fill in the appropriate fields, recommending the use of the same VPC subnet.
-
Utilize the provided AMI to establish a base PDC.
- The AMI can be updated later, and your own images will be visible, along with the latest Amazon Windows server image.
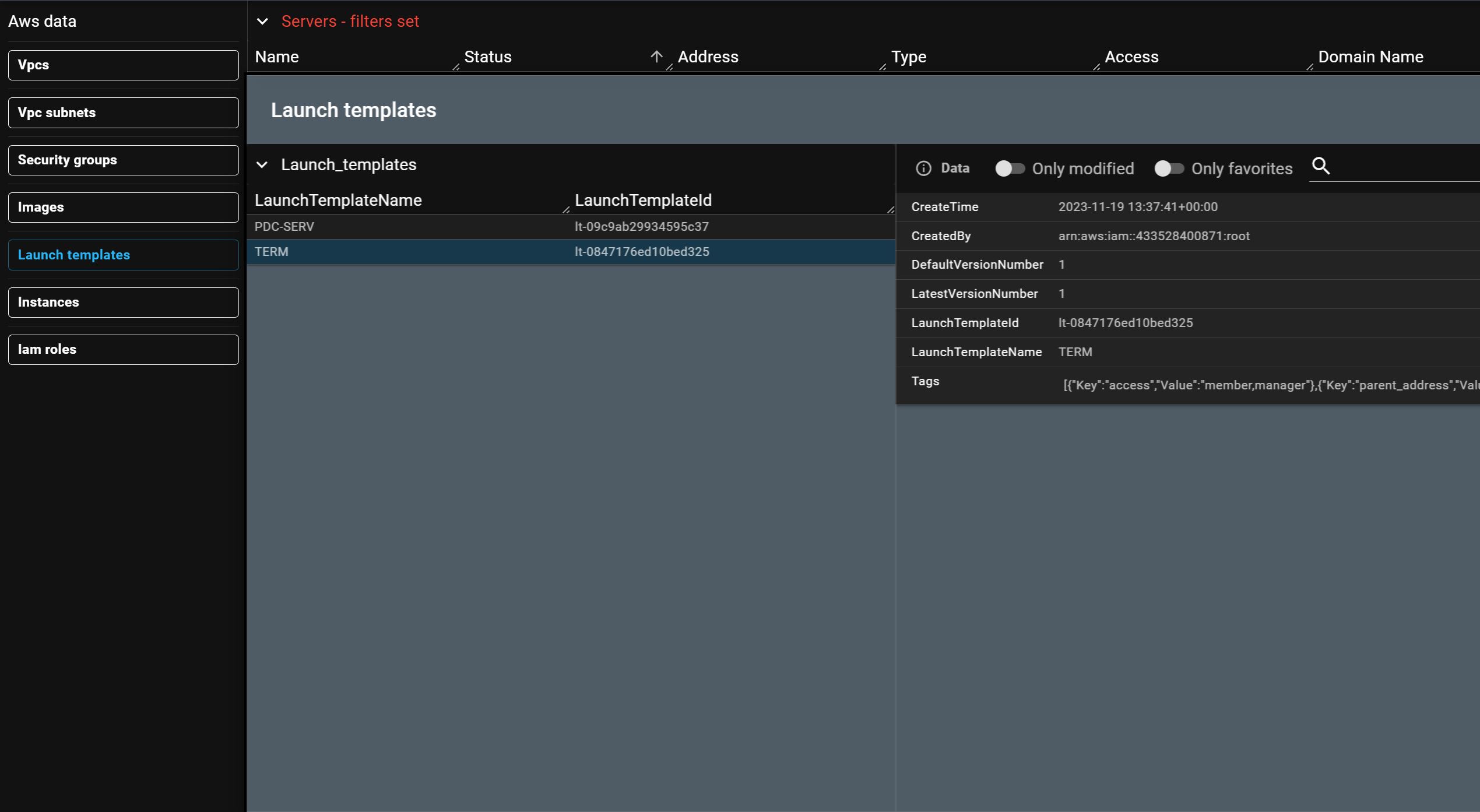
View launch templates from inside Taskforger and on AWS.
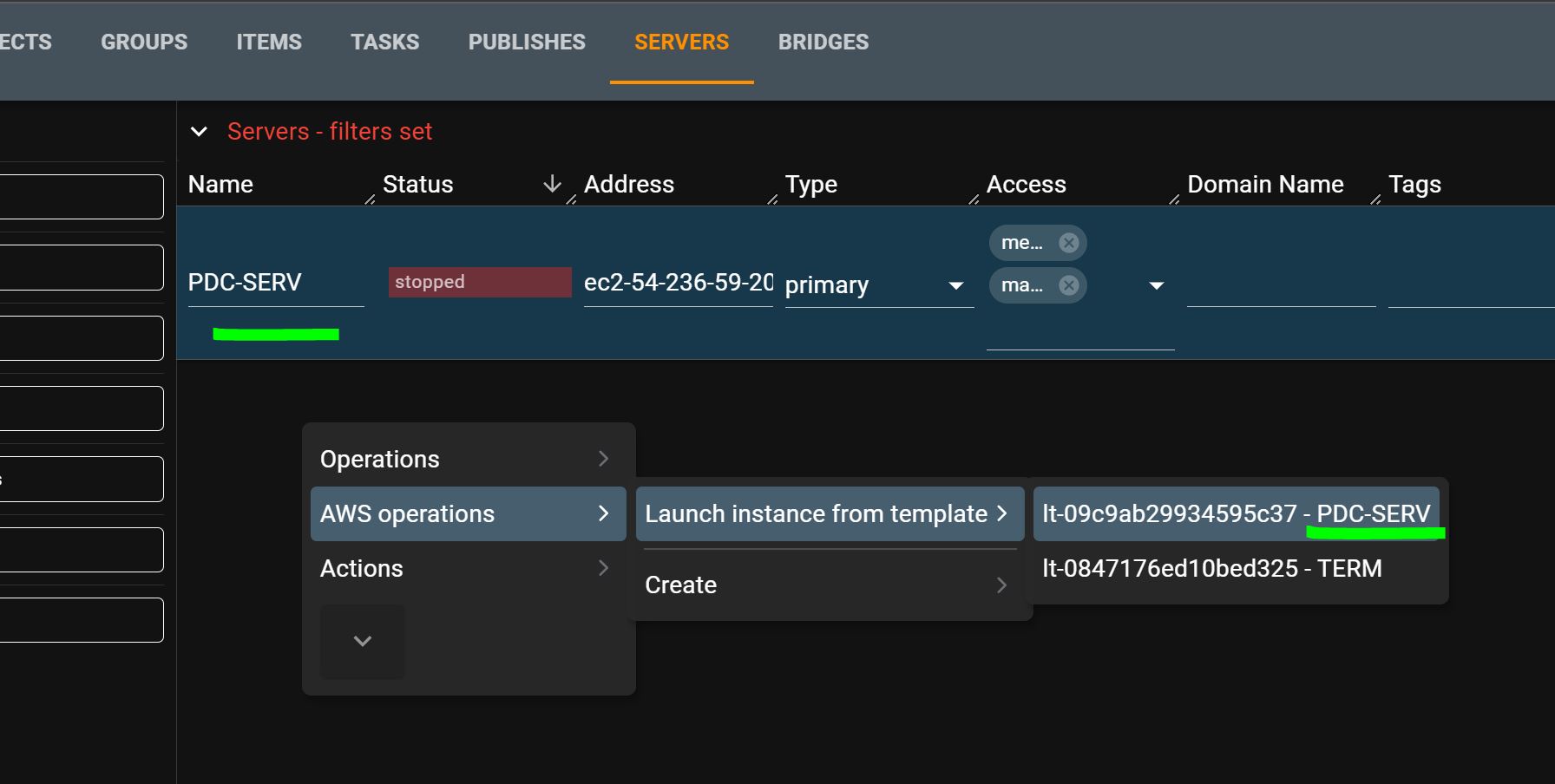
Launch PDC
- Right-click to access - AWS operations - Launch instance from template.
- Taskforger will automatically check AWS for new instances and add them.
Log in to your instance with RDP, retrieve the password from AWS using the .pem file, and confirm that Taskforger is running on the instance. Update the host map through the context menu.
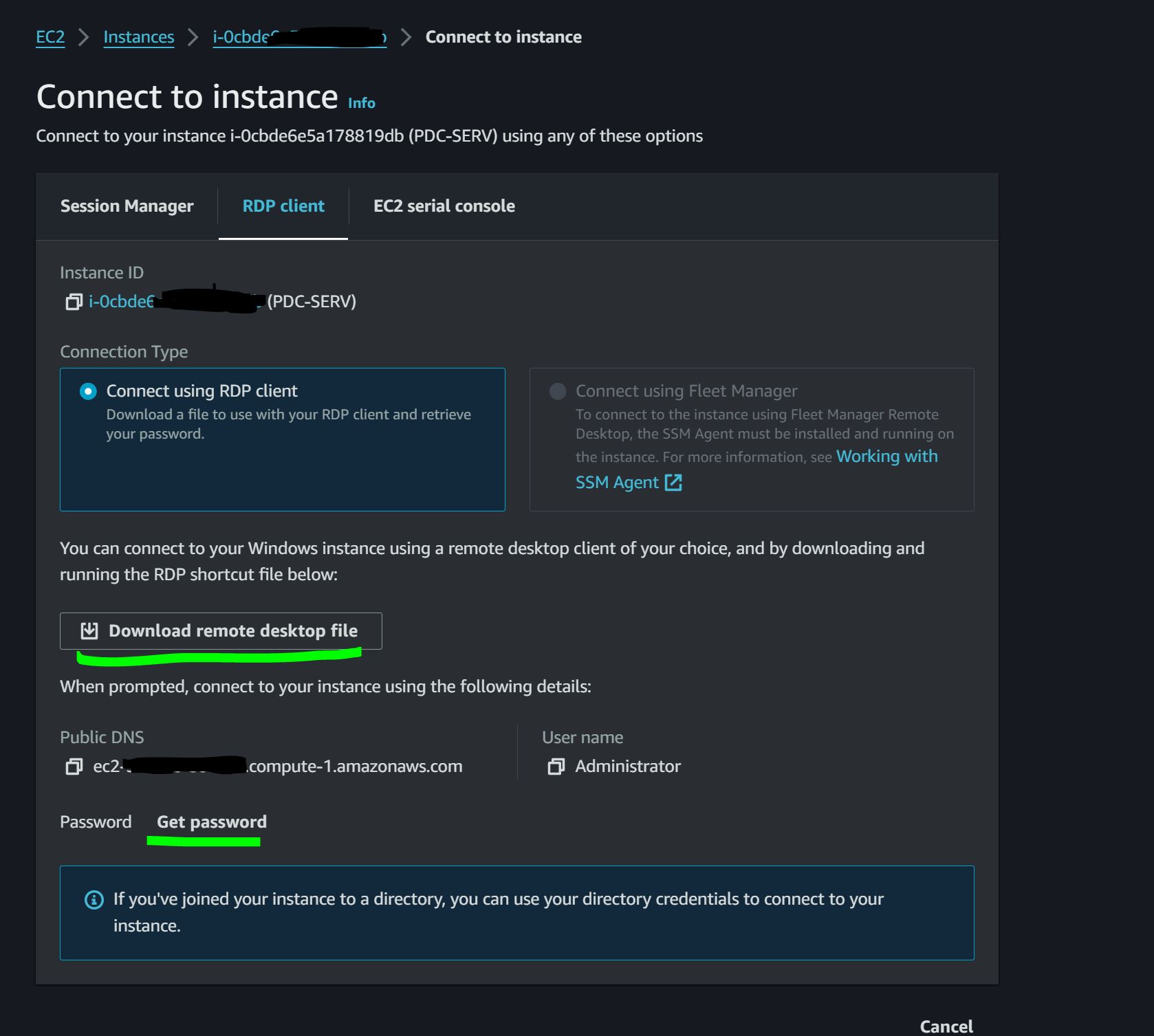
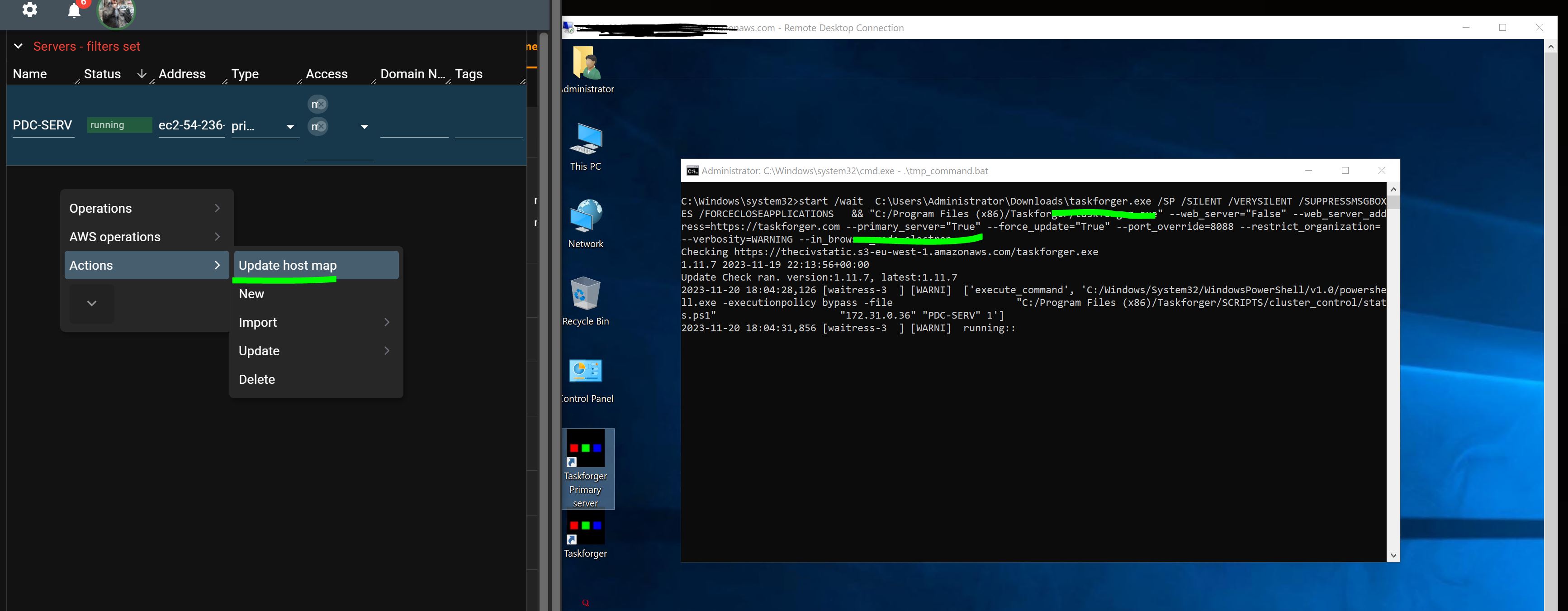
This is a good point to update your Administrator password. Your domain password is handled by the secrets manager; you should not update this as it is done automatically.
Create Terminal Launch Template
For terminal instances:
-
Select your PDC-SERV.
-
Right-click to access - Create - Launch Template.
-
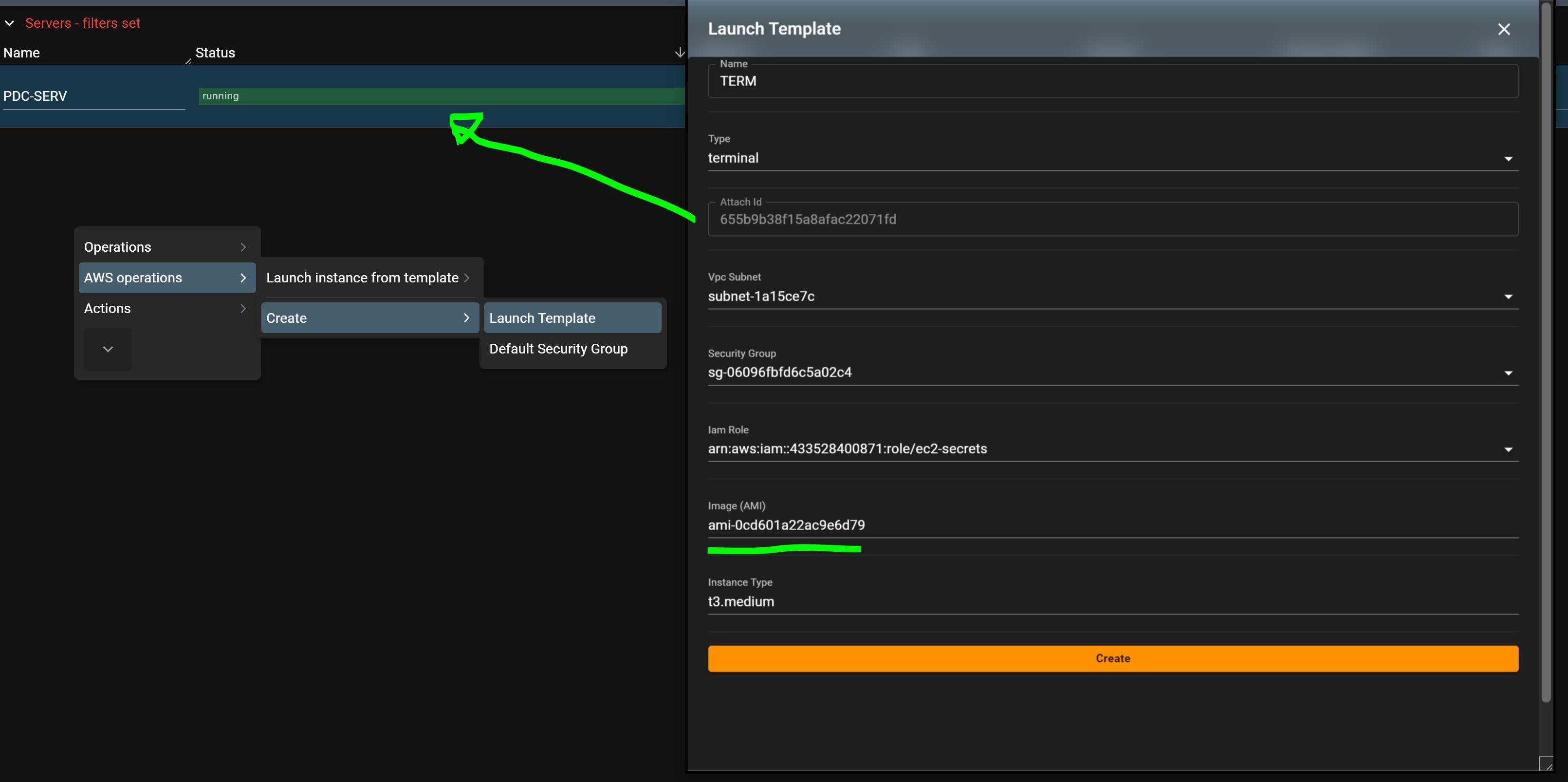
Fill in the appropriate fields, ensuring the type is 'terminal.' Attach ID will use the PDC-SERV ID.
-
It is recommended to use the same VPC subnet.
-
Choose the latest Windows AWS image.
- Later, this image can be configured with installed software.
Launch Terminal
- Right-click to access - AWS operations - Launch instance from template.

After a few minutes, your instance will boot and automatically connect to the domain. Connect through RDP with the Admin account or any domain user account.
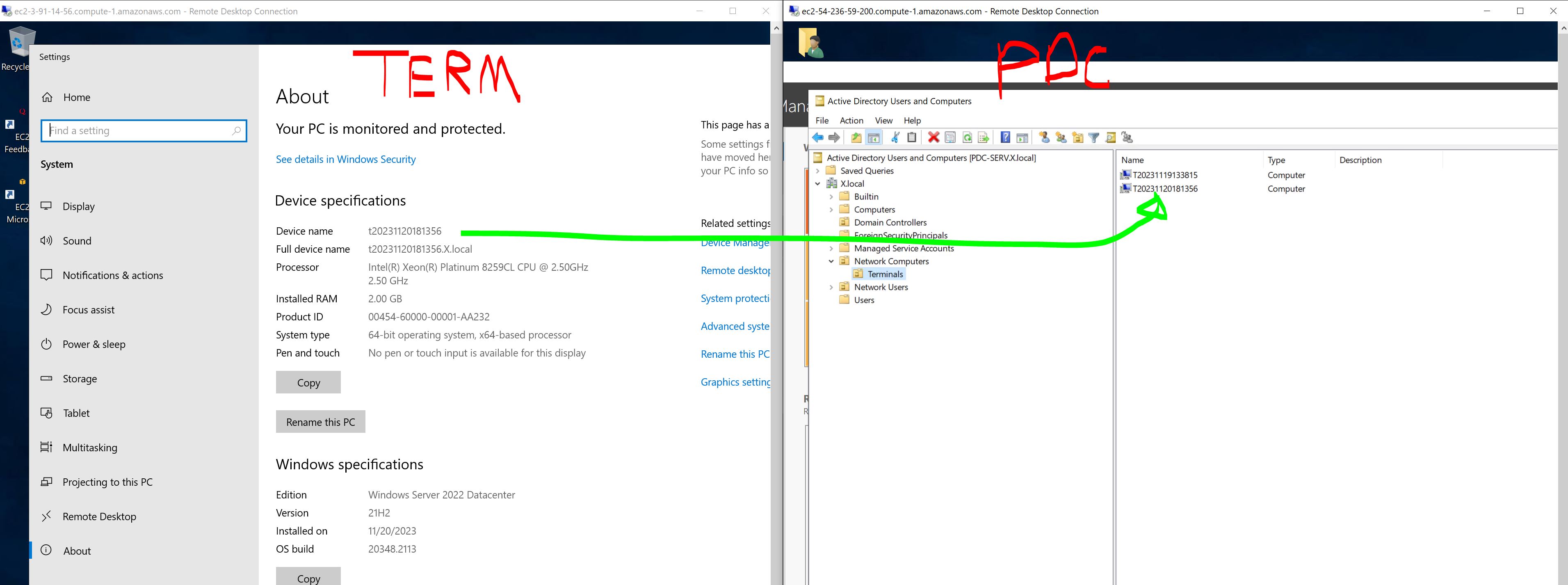
The instance will appear in Taskforger as it periodically checks AWS for new instances. Some values are set as tags on the launch template and the subsequent instances, updated in Taskforger.
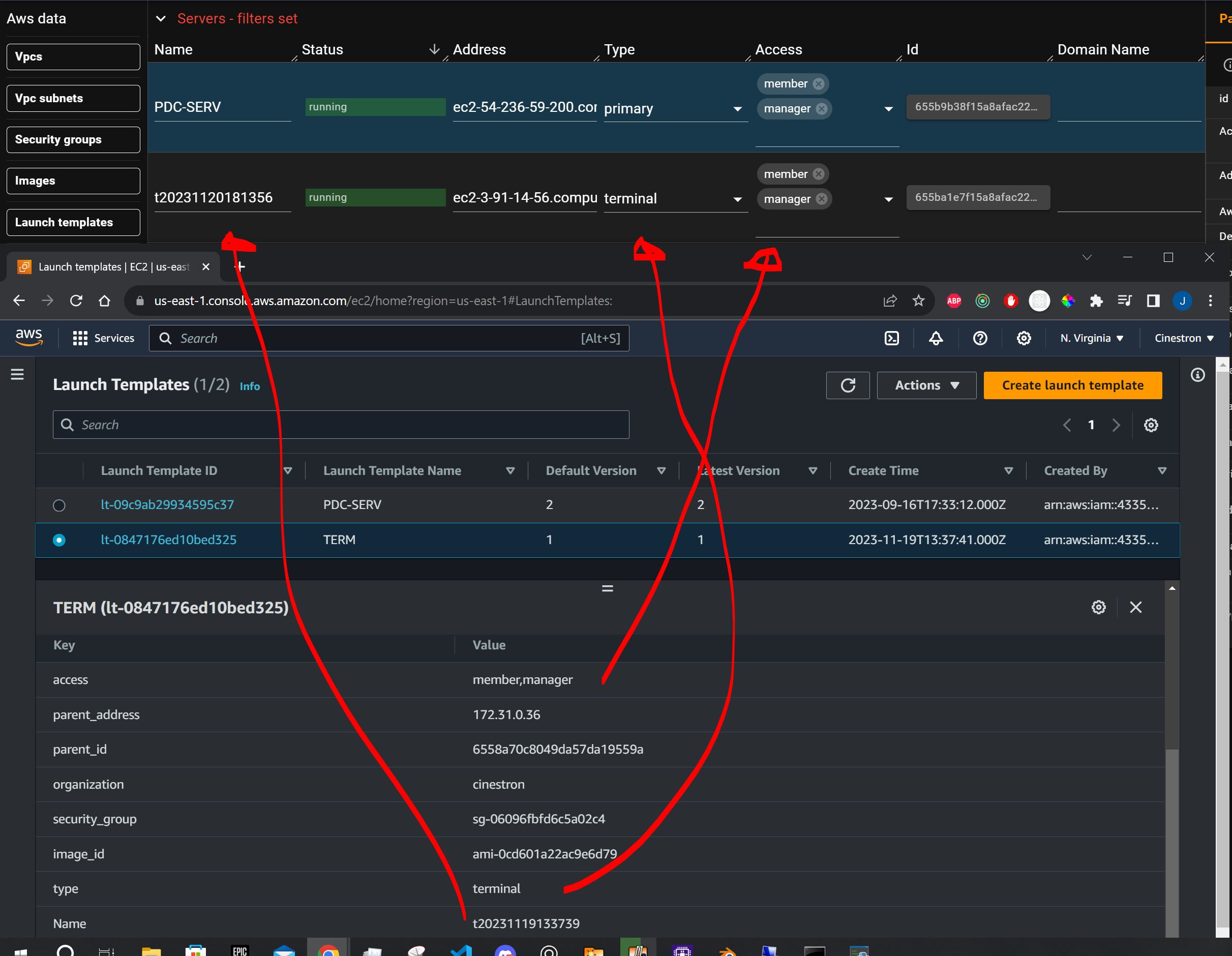
Stopping the PDC-SERV after creating a launch template will require creating a new launch template for the terminals or updating the tags manually, as IPs will change. Typically, keep your PDC-SERV running and only stop/start terminals as needed.
Conclusion
Congratulations! You now have a fully operational network on AWS with connection access from Taskforger. Other users in your organization do not need an AWS config to connect, only to create new instances.